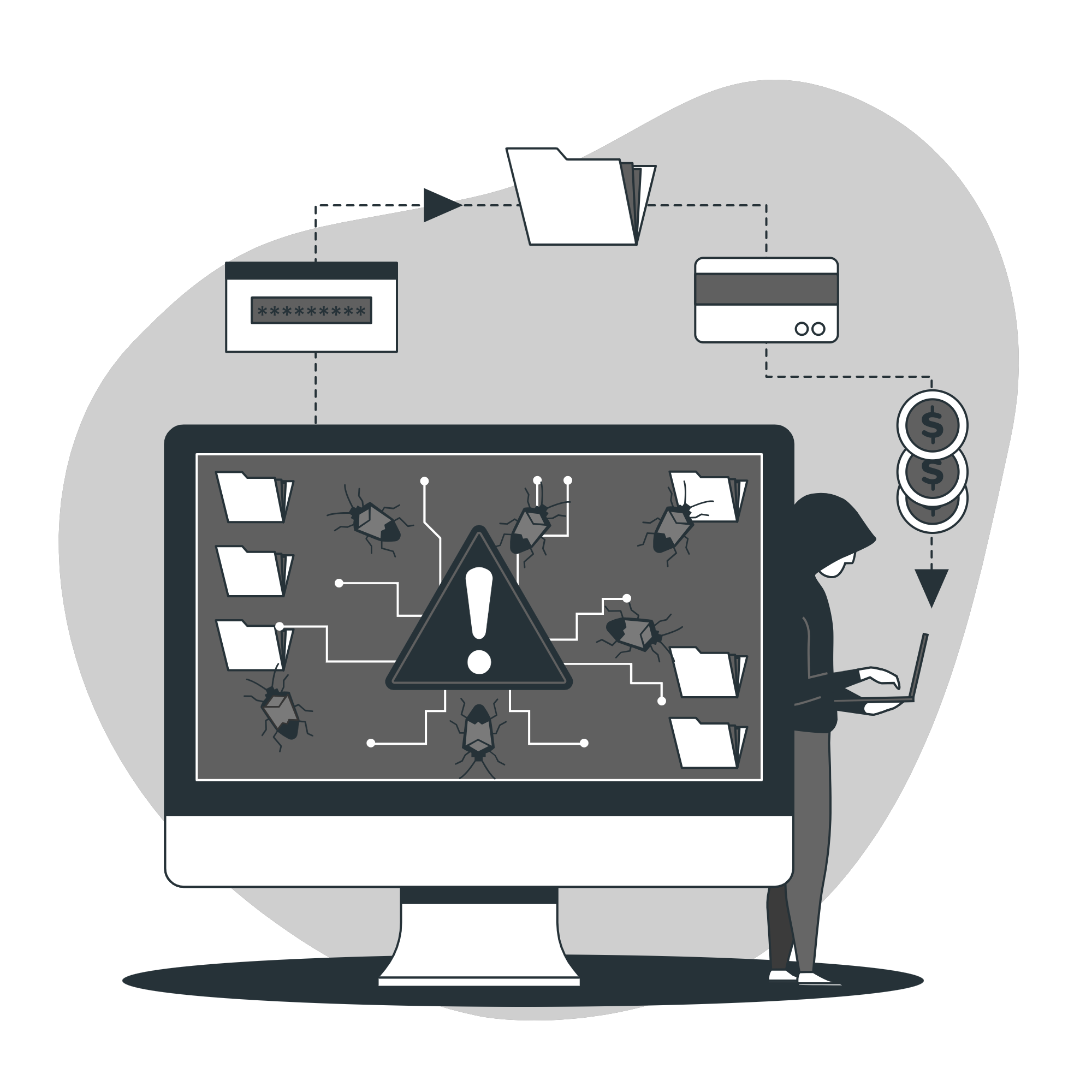
Challenges
-
Advanced Persistent Threats (APTs):
- Sophisticated adversaries employ techniques that evade conventional security measures, posing significant risks to organizations.
-
Data Overload:
- The influx of threat intelligence data from various sources can overwhelm security teams, making it challenging to extract actionable insights.
-
User Behavior Anomalies:
- Identifying deviations in user behavior is crucial for detecting insider threats and compromised accounts.
-
Integration and Scalability:
- Ensuring seamless integration with existing infrastructure and scalability to handle large data volumes are critical for effective threat management.